Social Networking Sites Open Gateway to Online Predators
The Internet provides a very good platform for online predators since they can easily hide their identity and get access to the target victims. An online predator can be defined as a criminal who targets teens with the aim of manipulating them to meeting for sex (Smith, 2009). Online predators masquerade to be building genuine friendship with victims through lying, blackmailing, and guilt. Additionally, they attempt to engage in intimate communication and eventual in-person meeting (Wolak, and Finkelhor, 2006). Online predators also use information on the profile page of the social site to try and locate the victim in person and engage them in a relationship. This is the reason why it is critical for one to evaluate the information to be included in the profile page to avoid predation. Predators “groom” to attract the victims into their trap. The national centre for missing and exploited children conducted research study on crime against children in 2006 and found the following about youth internet users for a period of five years (Wolak, and Finkelhor, 2006).
Visual script for online predation
- The rate of youth encountering unwanted sexual exposure to sexual materials increased from25% to 34% (Smith, 2009).
- There was an increasing rate of 6% to 9% of cases of online harassment
- There was a decrease from 19%- 13% in the number of those youths receiving unwanted solicitation for sex. This is attributed to proper measures taken against online predation.
- Forty percent (40%) of youth who use internet revealed that online sex solicitors asked for nude or sexually explicit photographs from them.
- Thirty one percent (31%) of the solicitors were very aggressive and they attempted offline contact with the youth (Smith, 2009).
Personal security risks caused by use of social networking site
Invasion on private life or personal security risks is one problem that social sites pose to internet users. If personal information, password to social sites pages and photos posted online are not carefully they can be used by other malicious intruders to jeopardize the reputation of individuals or invade personal securities of individuals (Wolak, and Finkelhor, 2006). Care must be taken so that information given online is limited to an extent of avoiding private life invasion by intruders or unnecessary persons. Malicious impersonation occurs when some people pretend to be the ones you really know but they are not the ones. Such people pretend to be your friend and befriend your children online leading to unfortunate consequences (Smith, 2009).
Conclusion
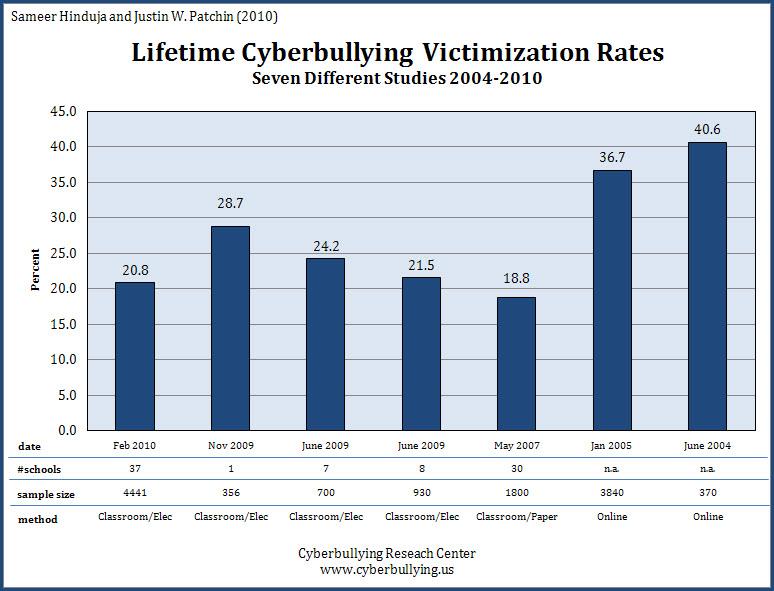
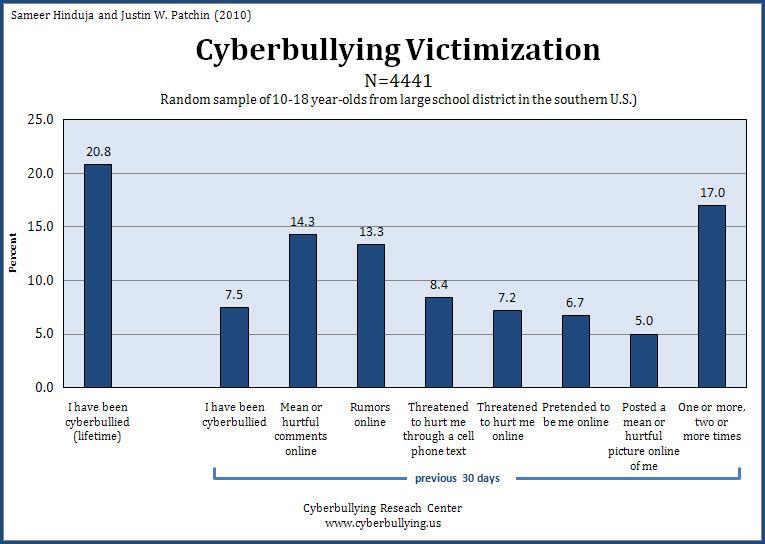
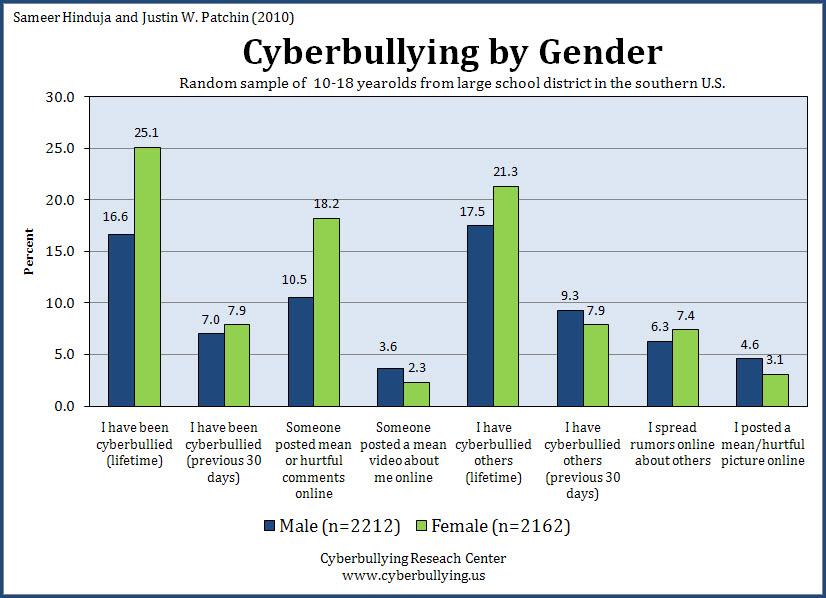
Cyber bulling, internet predators and personal security risks caused by use of social networking site is real and is on the increase as seen from above. The advent of social networking sites only accelerated the problems associated with internet crimes. The best way to curb or stop cyberbullying, online predation and personal security risk is by educating internet users to be careful about the information they reveal about them online (Wolak, and Finkelhor, 2006. Kids must be informed and guided by their parents not to give private information online because once they do so they risk themselves against burring and predation or invasion of their personal lives by intruders. Asking people to stop using social sites as a way to avoid cyberbullying, online predation and private live invasion is not the best way of dealing with the crimes or prosecuting the perpetrators of the crime still, is not the best way to deal with it rather everybody should be informed that the any personal/ private information provided online is never safe at all and is prone to online intrusion. However, perpetrators of cyberburrying or those people responsible for spreading rumors about other people or impersonating other people who do not have pages on social sites should be prosecuted and punished for causing harm to innocent victims (Smith, 2009).
More research should be done on cyberbullying so that strong measures can be developed to curb these crimes which are on the increase in the recent years. Most importantly the parents should be alert and informed about the social sites their children are operating so that they can easily monitor any kind of bullying or abuse resulting from the sites. They should encourage their kid stop report to them or seek for advice in case they encounter problems online. This will serve as the sets strategy to avoid may negative consequences of cyberbullying and other online crimes committed to kids.
References
Wolak, M. and Finkelhor, S. (2006). Online Victimization of Youth: Five Years Later. Alexandria, VA: National Center for Missing and Exploited Children
Smith, P. (2009). An investigation in to cyberbullying, its forms, awareness and impact, and the relationship between age and gender in cyber bullying. London: Oxford university press.




